Software Architecture: Beyond the Code
A comprehensive guide to software architecture explained in human language: patterns, organization, structure, and how to build systems that scale with your business.
Imagine you’re hired to design an office building. You don’t start by choosing the curtain color or deciding which computer brand to buy. First, you ask fundamental questions: How many people will work here? How will departments communicate with each other? What happens when the company grows? Where will basic services like electricity and water go? How do we evacuate the building in an emergency?
Software architecture is exactly the same. It’s not about what programming language to use or which framework is trendy. It’s about the fundamental decisions that will determine whether your system can grow, adapt, and survive the inevitable changes in business and technology.
I’ve seen companies spend millions building software that collapses when traffic doubles. I’ve seen systems that worked perfectly for 100 users but become unusable with 1,000. I’ve seen architectures so rigid that adding a new feature requires rewriting half the system. And I’ve also seen the opposite: well-architected systems that scale from thousands to millions of users without rewriting a single line of core business.
The difference isn’t in using more expensive technology or hiring more developers. It’s in the fundamental architectural decisions made at the beginning, and in the discipline to maintain those decisions as the system evolves.
What Software Architecture Really Is
Before talking about patterns or diagrams, you need to understand what architecture means in the context of software. It’s not just a set of boxes and arrows in a document nobody reads. It’s the set of structural decisions that determine how your system is built, deployed, and evolves.
Architecture is the decisions that are hard to change.
When you choose to use a monolith versus microservices, that’s architecture. When you decide how system components will communicate, that’s architecture. When you define where data will live and how it will be accessed, that’s architecture. These are the decisions that, if you get wrong, will cost months or years to correct.
“Software architecture is about the things you wish you’d done right from the start”
But here’s the paradox: the best architectural decisions are made when you have the most information about your system, but that’s later when it’s harder to change them. That’s why good architecture isn’t the one that makes all perfect decisions from day one, but the one that allows you to postpone decisions until you have enough information, and change them when necessary.
The Three Pillars of All Architecture
All software architecture is built on three fundamental pillars. Understanding these pillars helps you evaluate any architectural decision, regardless of the specific pattern you use.
Pillar 1: Separation of Concerns
The problem: When everything is mixed in one place, changing something breaks something else. Your presentation code is intertwined with your business logic, which is mixed with your data access. It’s like having all electrical cables, water pipes, and ventilation ducts running through the same tunnel without any separation.
The principle: Each part of the system must have a clear and unique responsibility. Presentation handles showing information to the user. Business logic handles the rules that define your domain. Data access handles persisting and retrieving information. Each does its job and only its job.
Why it matters: When responsibilities are separated, you can change the user interface without touching business logic. You can change the database without modifying business rules. You can test each part independently. The system becomes modular in the true sense of the word.
A real-world example: Imagine a hotel reservation system. The responsibility of displaying available rooms (presentation) is separated from the rules about which rooms can be reserved according to user type (business logic), which is separated from how reservations are saved in the database (persistence). If tomorrow you want to add a mobile app, you only need a new presentation layer. Business rules and data don’t change.
Pillar 2: Dependency Management
The problem: System components need to interact with each other. But if A depends directly on B, and B depends on C, you end up with a dependency chain where changing C breaks the entire system. Worse, if dependencies go in all directions, you end up with a “big ball of mud” where everything depends on everything.
The principle: Dependencies must flow in one direction: toward the center, toward what’s most stable, toward business rules. Outer layers (interfaces, databases, external services) can depend on inner layers, but inner layers should know nothing about outer ones.
Why it matters: When dependencies are well managed, you can replace external components without affecting the system core. Your business logic doesn’t depend on your specific database, so you can change from PostgreSQL to MongoDB if necessary. Your system doesn’t depend on a specific web framework, so you can migrate without rewriting everything.
A real-world example: In a billing system, your business logic defines how taxes, discounts, and totals are calculated. This logic shouldn’t depend on whether you use React or Angular in the frontend, or whether data is in SQL or NoSQL. The dependency direction is: frontend depends on business logic, database depends on business logic, but business logic depends on no one. It’s autonomous.
Pillar 3: Clear Boundaries
The problem: Without clear boundaries, components leak into each other. UI code starts containing business logic. The data layer starts making business decisions. Everything becomes a spaghetti mess where you don’t know where one component ends and another begins.
The principle: Each component or module must have well-defined boundaries: clear public interfaces that define how other components can interact with it, and private implementation details that no one else can see or use.
Why it matters: Clear boundaries give you encapsulation. You can completely change a component’s internal implementation without affecting anyone else, as long as the public interface remains the same. This is fundamental to being able to evolve the system without everything breaking.
A real-world example: In an e-commerce system, the payment processing component has a very simple public interface: “process payment with this information.” Internally, it could be using Stripe, PayPal, or your own system. Tomorrow you can completely change the payment provider, and as long as the public interface is the same (receives the same information, returns the same type of response), no other system component needs to change.
Fundamental Architectural Patterns
Now that you understand the pillars, let’s look at the most important architectural patterns. Each is a different way to organize your system, with its own trade-offs.
Layered Architecture
The central idea: You organize your system in horizontal layers, where each layer can only communicate with the layer directly below it. It’s like a building: each floor is built on the previous one, and you can only access the floor below using the defined stairs or elevators.
Typical layers:
Presentation Layer: This is the visible face of your system. Where the user interface lives, the REST APIs that clients consume, command-line interfaces. Its only responsibility is to take user input, pass it to lower layers, and present results.
In an online banking system, this layer contains:
- Screens where users see their balance
- Forms to transfer money
- API endpoints that the mobile app queries
- Handlers that receive HTTP requests and convert them into business layer calls
Business Logic Layer: Here live the rules that define your domain. If you run a bank, these rules include: which accounts can transfer to which other accounts, what’s the daily transfer limit, what fees apply, how interest is calculated.
This layer knows nothing about HTTP, JSON, or HTML. It doesn’t know if it’s being used by a web application, mobile app, or batch process. It only knows business rules.
Persistence Layer: This layer handles saving and retrieving data. It knows SQL, knows how to connect to the database, how to optimize queries, how to handle transactions. But it doesn’t make business decisions.
When the business layer says “I need information about this account,” the persistence layer gets it from wherever it’s stored, without the business layer knowing if it comes from PostgreSQL, MongoDB, or a file.
Infrastructure Layer: Technical details live here. How you connect to external services, how you send emails, how you process files. These are utility services that other layers need but aren’t part of the business.
When to use this architecture:
- When your system has natural separations of responsibility
- When your team is relatively small and can work across all layers
- When simplicity is more important than maximum scalability
- When you’re building traditional enterprise applications
When not to use it:
- When you need to scale components independently
- When different parts of the system have very different workloads
- When multiple large teams need to work without blocking each other
The real challenge: The biggest problem with layered architecture is the tendency to “jump” layers. A developer pressed for time makes the presentation layer talk directly to the database, skipping business logic. Once this starts, the architecture erodes quickly.
Microservices Architecture
The central idea: Instead of a monolithic system, you build multiple small, independent services, each responsible for a specific business capability. Each service is a complete program that can be deployed, scaled, and maintained independently.
How it’s organized:
Services by Business Domain: Each service aligns with a business capability. In an e-commerce:
- Catalog Service: Manages products, categories, search
- Cart Service: Handles active shopping carts
- Orders Service: Processes orders, manages their state
- Payments Service: Processes financial transactions
- Shipping Service: Coordinates delivery logistics
- Users Service: Manages authentication and profiles
Each is completely independent. It has its own database, its own code, its own deployment cycle.
Communication Between Services: Services communicate with each other in two main ways:
Synchronous Communication (REST/gRPC APIs): One service makes a request to another and waits for a response. The Orders service calls the Payments service to process a payment. It’s direct but creates temporal coupling: if the Payments service is down, the Orders service can’t complete orders.
Asynchronous Communication (Messages/Events): A service publishes events about things that happened, other services subscribe to events they’re interested in. When an order completes, the Orders service publishes an “OrderCompleted” event. The Shipping service listens to this event and automatically creates a shipping task. The Notifications service listens to the same event and sends a confirmation email.
Data Management: Each service has its own database. The Catalog service cannot directly access the Orders service database. If it needs order information, it must request it through the Orders service API.
This data separation is fundamental but complicated. What happens if you need a report that crosses data from multiple services? That’s where patterns like Event Sourcing or CQRS come in.
When to use microservices:
- When your organization is large enough for independent teams
- When different parts of the system have very different scalability requirements
- When you need to deploy parts of the system independently
- When you have DevOps maturity to manage multiple services
When not to use them:
- When your team is small (less than 10-15 people)
- When your system is relatively simple
- When you have no experience with distributed systems
- When you don’t have robust CI/CD infrastructure
The hidden cost: Microservices shift complexity. Instead of complexity in code (the monolith), you have complexity in the network, coordination, distributed debugging, and transactions that cross services. It’s not simpler, it’s just different.
Event-Driven Architecture
The central idea: Instead of components calling each other directly, they publish events about things that happened, and other components react to those events. It’s like a notification system: when something important happens, it’s announced, and whoever is interested can react.
How it works:
Event Producers: These are components that detect when something significant occurs and publish an event. In a video streaming system:
- When a user registers → Event: “UserRegistered”
- When a user starts watching a video → Event: “VideoStarted”
- When a user finishes a video → Event: “VideoCompleted”
- When a user cancels their subscription → Event: “SubscriptionCancelled”
Producers only publish the event. They don’t know or care who listens to it.
Event Bus: This is the channel through which events flow. It can be a technology like Kafka, RabbitMQ, or cloud services like AWS EventBridge. It’s like the postal system: producers deposit events, consumers pick them up.
Event Consumers: These are components that listen for specific events and react. Multiple consumers can listen to the same event:
When “UserRegistered” is published:
- The Email service sends a welcome email
- The Analytics service records a new user in metrics
- The Recommendations service creates an initial profile
- The CRM service adds the user to marketing campaigns
All react to the same event, but each does something different. If you add a new consumer tomorrow, producers and other consumers don’t know.
Event Processing:
Simple Processing: Each event is processed independently. When “VideoCompleted” arrives, you update the user’s history and that’s it.
Stream Processing: You process continuous event streams, looking for patterns. “This user has started 10 videos but hasn’t completed any in the last week” → Event: “UserEngagementDropping” → The Retention service sends personalized content.
Event Sourcing: Instead of saving current state, you save all events that led to that state. You don’t save “the account balance is $500,” you save all events: “deposited $1000,” “withdrew $300,” “withdrew $200.” You can reconstruct current state by replaying events, and you have complete history of everything that happened.
When to use event-driven architecture:
- When you need high decoupling between components
- When multiple parts of the system need to react to the same events
- When you need complete audit of everything that happens
- When different parts of the system process at different speeds
When not to use it:
- When you need strict transactional consistency
- When your system flow is mainly request-response
- When your team isn’t familiar with eventual consistency
- When debugging and observability are challenges you can’t handle
The complexity of asynchrony: The biggest challenge is that you lose the simplicity of “I do A, then B, then C.” Now it’s “I publish event A, eventually B, C, and D happen, in some order.” Debugging becomes harder: why didn’t the user receive their welcome email? Was the event published? Did it reach the bus? Did the consumer process it? Was the email service available?
Hexagonal Architecture (Ports and Adapters)
The central idea: Your business logic is at the center, completely isolated from the outside world. All contact with the outside world (databases, APIs, user interfaces) is done through “ports” (interfaces) and “adapters” (implementations).
The structure:
The Core (Central Hexagon): Here lives your pure business logic. The rules that define your domain, the operations your system can perform. It doesn’t matter how it’s used or where it’s deployed.
In a library management system:
- Entities: Book, User, Loan
- Rules: A user can have maximum 5 borrowed books, loan period is 14 days, there are late fees
- Operations: Lend book, return book, renew loan, calculate fees
This core knows nothing about REST, SQL, or graphical interfaces.
Ports (Interfaces): These are connection points with the outside world. There are two types:
Inbound Ports (Driving Ports): Define what operations users or external systems can do with your system. They’re the use cases your system supports.
Port: LibraryService
- lendBook(userId, bookId)
- returnBook(loanId)
- renewLoan(loanId)
- consultLoans(userId)Outbound Ports (Driven Ports): Define what your core needs from the outside world. Typically these are repositories for data or integrations with external systems.
Port: BookRepository
- findBookById(id)
- findAvailableBooks()
- saveBook(book)
Port: NotificationService
- sendReminder(user, message)The core defines these interfaces, but doesn’t implement them.
Adapters: These are concrete implementations of ports. They live outside the hexagon.
Inbound Adapters: Translate from the outside world to your domain.
- REST Adapter: Receives HTTP requests, converts them into LibraryService calls
- CLI Adapter: Reads console commands, converts them into service calls
- GraphQL Adapter: Receives GraphQL queries, translates them into domain operations
Outbound Adapters: Implement the interfaces your core needs.
- PostgreSQL Adapter: Implements BookRepository using PostgreSQL
- MongoDB Adapter: Implements BookRepository using MongoDB (same port, different adapter)
- Email Adapter: Implements NotificationService by sending emails
- SMS Adapter: Implements NotificationService by sending SMS
Why it’s powerful: You can change any adapter without touching the core. You can have multiple adapters for the same port: your system exposes both REST API and GraphQL, both talking to the same core. For testing, you use in-memory adapters that are super fast.
When to use hexagonal architecture:
- When business logic is complex and valuable
- When you need flexibility to change technologies
- When you want to test business logic independently
- When multiple interfaces need to use the same logic
When not to use it:
- When your application is mainly CRUD without complex logic
- When initial development speed is critical
- When your team isn’t familiar with the pattern
The required learning: The biggest challenge isn’t technical but mental. It requires discipline to keep the core pure, without letting implementation details leak in. It requires thinking about interfaces before implementations. Many teams start with good intentions but gradually let frameworks and databases “leak” into the core.
Organizing Your System: From Components to Ecosystems
Architecture isn’t just abstract patterns. It’s how you physically organize your code, your services, and your teams.
Code Organization
By Technical Layers (Traditional):
project/
controllers/
UserController
OrderController
ProductController
services/
UserService
OrderService
ProductService
repositories/
UserRepository
OrderRepository
ProductRepositoryThe problem: To add “Users” functionality, you touch three different folders. Related files are scattered.
By Business Domains (Modern):
project/
users/
UserController
UserService
UserRepository
User (entity)
orders/
OrderController
OrderService
OrderRepository
Order (entity)
products/
ProductController
ProductService
ProductRepository
Product (entity)The advantage: Everything related to Users is together. You can work on the users module without touching anything else. Boundaries between modules are clear.
Taken to the extreme (Microservices): Each module becomes a completely independent service, with its own repository, its own deployment pipeline, possibly its own programming language.
Team Organization
Your system architecture should reflect how your team is organized. This is Conway’s Law:
“Organizations which design systems are constrained to produce designs which are copies of the communication structures of these organizations”
Teams by Technical Layers: A frontend team, a backend team, a database team. To implement a feature, all three teams must coordinate. Dependencies cross teams.
Teams by Product/Domain: Each team owns a complete business domain. The “Checkout” team has frontend, backend, and data for the entire checkout process. They can move fast because they have everything they need.
Which is better? It depends on your organization. If you have 10 people, everyone probably works on everything. If you have 100, you need division. The general rule: organize teams around business functionalities, not technologies.
Bounded Contexts: Boundaries in Large Systems
In large systems, the same concept means different things in different parts of the system. “Product” means one thing in the catalog (SKU, price, inventory) and something different in the shopping cart (selected item with quantity).
The solution: Bounded Contexts Divide your system into bounded contexts, each with its own domain model. The “Product” model in the Catalog context is different from the model in the Shopping context, and that’s okay.
Context Mapping: Explicitly define how contexts relate:
- Shared Kernel: Two contexts share a small common model
- Customer-Supplier: One context depends on another, the supplier provides API for the customer
- Conformist: One context accepts another context’s model as is
- Anticorruption Layer: One context translates another’s model to protect its own model
Why it matters: Without clear bounded contexts, you end up with a giant “domain model” that tries to serve everyone, resulting in a disaster that serves no one well. With bounded contexts, each part of the system has the model it needs.
Scalability: Designing for Growth
An architecture that works for 100 users can collapse with 10,000. You need to think about scalability from the beginning, not as something you’ll “fix later.”
Vertical vs Horizontal Scalability
Vertical (Scaling Up): Add more power to your server: more CPU, more RAM, faster disks. Simple but has limits. You can only make a server so big. It’s like putting a more powerful engine in your car.
Horizontal (Scaling Out): Add more servers. More complex but no theoretical limits. Instead of one giant server, you have 10, then 100, then 1000 normal servers working together. It’s like adding more cars instead of making one super powerful.
Stateless Components: To scale horizontally, your components must be stateless. They don’t store session information locally. Any request can be handled by any server.
Shared State: State (user sessions, caches) moves to systems designed for that: Redis for caches and sessions, databases for persistence.
Load Balancing: A load balancer distributes requests among multiple instances of your service. If a server fails, requests go to others. If you need more capacity, you add more servers behind the load balancer.
Scalability Patterns
Multi-Level Caching:
Client Cache: The browser stores static resources: images, CSS, JavaScript. It doesn’t need to request them each time.
CDN Cache: Content Delivery Networks serve content from servers geographically close to the user. A user in Mexico receives images from a server in Mexico, not from one in Virginia.
Server Cache: Frequently accessed data is stored in Redis or Memcached. Instead of complex database queries, we read from cache in milliseconds.
Database Cache: The database itself stores recent queries in memory.
Cache Invalidation: The hard problem: when does cache expire? How do you ensure users see updated data? There are no easy answers, only trade-offs between consistency and performance.
Data Partitioning (Sharding): When your database is too big for one server, you divide it. Users with IDs 1-1000000 go to one server, 1000001-2000000 to another.
The challenge: How do you make queries that cross shards? How do you rebalance when one shard grows more than others?
Read-Write Segregation (CQRS): Reads and writes have different patterns. You separate models: one model optimized for writes, another optimized for reads.
Command Side (Write): Normalized model, ACID transactions, strict validations.
Query Side (Read): Denormalized models, optimized for specific queries. Updates asynchronously from Command Side.
The benefit: Scale reads and writes independently. Optimize each side for its purpose.
The cost: Eventual consistency. Read data is slightly out of date.
Designing for Failures
In distributed systems, failures aren’t exceptional, they’re normal. You design expecting things to fail.
Circuit Breaker: If a service is failing repeatedly, you stop calling it temporarily. It’s like an electrical fuse that trips to protect the system.
When the payments service fails 5 times in a row:
- The circuit breaker “opens”
- Following requests fail immediately without trying to call the service
- After a time, it tries a test request
- If successful, the circuit breaker “closes” and traffic resumes
Graceful Degradation: When something fails, the system continues working with reduced functionality.
If the recommendations service is down:
- Instead of showing personalized recommendations, you show popular products
- The page works, just with less personalization
Timeouts and Retries: You don’t wait indefinitely for responses. You have configured timeouts. If something fails, you try again, but with exponential backoff to not overload services that are already struggling.
Security in Architecture
Security isn’t something you add later. It must be woven into architecture from the beginning.
Defense in Depth
You don’t trust a single line of defense. You have multiple layers:
Perimeter (Firewall, WAF): The first line of defense. Blocks malicious traffic before it reaches your application.
Authentication and Authorization: You verify who the user is (authentication) and what they can do (authorization). You don’t trust client data. You validate on the server.
Encryption: Data in transit (HTTPS/TLS) and at rest (database encryption). Even if someone intercepts data, they can’t read it.
Input Validation: You never trust input data. You validate, sanitize, and escape everything. SQL injection, XSS, and other attacks exploit unvalidated input.
Principle of Least Privilege: Each component has only the permissions it absolutely needs. Your reporting service doesn’t need write permissions on the production database.
Zero Trust Architecture
You don’t automatically trust anything, even within your network.
Continuous Verification: Every request is verified, regardless of where it comes from. You don’t assume “internal” requests are safe.
Micro-Segmentation: Even services on the same network can’t talk to each other freely. Every communication goes through authentication and authorization verification.
Complete Audit: You log everything. Who accessed what, when, from where. If there’s a breach, you can track exactly what was compromised.
The Human Factor: Architecture and Organization
The best technical architecture fails if it doesn’t consider the human factor.
Cognitive Load
Every developer has a limit on how much they can keep in their head. An architecture that requires every developer to understand 50 different services to make a simple change is unsustainable.
Reduce Cognitive Load:
- Well-encapsulated modules with clear interfaces
- Up-to-date documentation
- Consistent standards across services
- Development tools that hide complexity
Evolutionary Architecture
You don’t design perfect architecture from day one. You design an architecture that can evolve.
Fitness Functions Metrics: You define automated metrics that verify your architecture stays healthy:
- Do dependencies continue flowing in the correct direction?
- Do build times remain reasonable?
- Do response times stay under certain thresholds?
When these metrics fail, you know the architecture is eroding.
Architectural Refactoring: You don’t wait for architecture to be broken to fix it. You regularly dedicate time to incrementally improve it.
Inverse Conway’s Law
If Conway’s Law says architecture reflects organization, the inverse is that you can change your organization by changing your architecture.
Want more autonomous teams? Design well-encapsulated services that minimize dependencies between teams.
Want teams to collaborate more? Design shared components that require coordination.
Documenting Architecture
Architecture only serves if it’s documented so others can understand and follow it.
C4 Model (Context, Containers, Components, Code)
Level 1 - System Context: High-level view showing your system and how it interacts with users and external systems. A diagram anyone can understand, even non-technical people.
Level 2 - Containers: The main containers that make up your system: web applications, mobile applications, databases, message queues. How they communicate.
Level 3 - Components: Within each container, the main components and their responsibilities.
Level 4 - Code: Class diagrams and implementation details. Only for complex components that justify it.
Why C4: It gives you clear vocabulary to talk about architecture at different levels of detail. With a PM you talk about Level 1. With your team you talk about Levels 2 and 3. In code review you talk about Level 4.
Architecture Decision Records (ADRs)
You document important architectural decisions:
Title: “Use PostgreSQL as main database”
Context: We need persistence for transactional data with complex relationships.
Decision: We will use PostgreSQL as our main database.
Consequences:
- Positive: ACID, complex relationships, maturity, rich ecosystem
- Negative: Harder to scale than NoSQL, requires schema design upfront
- Risks: We might need to complement with NoSQL for certain use cases
Alternatives Considered:
- MongoDB: Discarded because we need complex transactions
- MySQL: Discarded because PostgreSQL has features we’ll need (JSON, full-text search)
Why ADRs: In 6 months, when someone asks “why do we use PostgreSQL?”, you have the answer documented with all context. You don’t depend on tribal memory.
Tools and Resources
Software architecture is a deep field. This article is an introduction, but there’s much more to explore.
Fundamental Reading
“Software Architecture in Practice” by Bass, Clements, Kazman The definitive academic book on architecture. Dense but complete.
“Building Microservices” by Sam Newman The practical guide to microservices. Not just the what, but the how and when.
“Domain-Driven Design” by Eric Evans Fundamental for understanding how to organize complex systems around the business domain.
“Designing Data-Intensive Applications” by Martin Kleppmann Explains the fundamentals of distributed systems, databases, and data processing at scale.
Concepts to Dive Deeper
CAP Theorem In distributed systems, you can only have two of three: Consistency, Availability, Partition Tolerance. Understanding this is fundamental for designing distributed systems.
Eventual Consistency In asynchronous distributed systems, data will eventually be consistent, but not immediately. How to design with this constraint.
Service Mesh Dedicated infrastructure to handle communication between services: load balancing, service discovery, observability, security.
API Gateway Pattern A single entry point for multiple services, handling authentication, rate limiting, routing, and composition.
Communities and Continuous Learning
Architecture Conferences: QCon, O’Reilly Software Architecture Conference, GOTO Conference. Talks are available online.
Tech Company Blogs: Netflix Tech Blog, Uber Engineering, Airbnb Engineering. How they solve architecture problems at scale.
Case Studies: Read about real system architectures. How Netflix went from monolith to microservices. How Spotify organizes teams and systems.
Software architecture isn’t a document you write at the beginning and store in a drawer. It’s a set of decisions you make continuously, refining as you learn more about your domain, your users, and your constraints.
I’ve seen brilliant teams build beautiful architectures on paper that fail in reality because they didn’t consider team or business constraints. And I’ve seen “imperfect” architectures succeed tremendously because they were pragmatic about trade-offs.
Perfect architecture doesn’t exist. There’s architecture appropriate for your context: your team size, your domain complexity, your scale requirements, your organizational maturity. A 5-person startup shouldn’t architect like Netflix. But Netflix didn’t start with its current architecture either.
“Architecture is more about knowing what questions to ask than about knowing all the answers”
Your job as an architect isn’t to memorize patterns and apply them blindly. It’s to deeply understand your context, ask the right questions, evaluate trade-offs honestly, and make informed decisions you can adapt as you learn more.
Start simple. Add complexity only when you need it, not because you anticipate you might need it. But design so that adding that complexity later doesn’t require rewriting everything. That’s the balance: simple but evolvable.
The best architecture is the one that allows your business to grow without software becoming the obstacle. It’s the one that allows your team to be productive without drowning in complexity. It’s the one you can explain on a napkin but that scales to millions of users.
That’s the art of software architecture: building systems that solve real problems, with appropriate complexity, that can evolve over time. It’s not magic, it’s discipline, knowledge, and a lot of pragmatism.
Tags
Related Articles

Design Patterns: The Shared Vocabulary of Software
A comprehensive guide to design patterns explained in human language: what they are, when to use them, how to implement them, and why they matter for your team and your business.
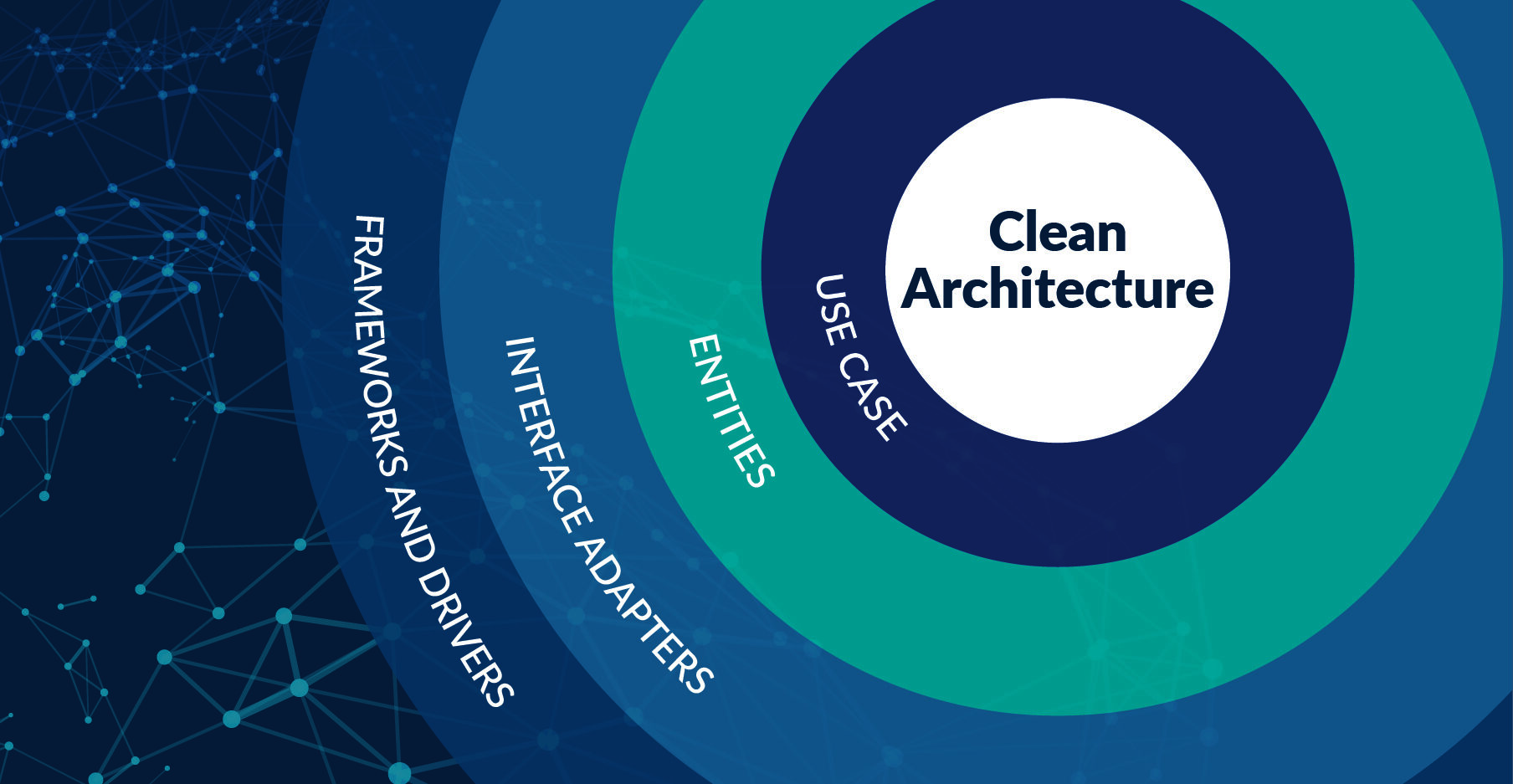
Clean Architecture: Building Software that Endures
A comprehensive guide to Clean Architecture explained in human language: what each layer is, how they integrate, when to use them, and why it matters for your business.

gRPC: The Complete Guide to Modern Service Communication
A comprehensive theoretical exploration of gRPC: what it is, how it works, when to use it, when to avoid it, its history, architecture, and why it has become the backbone of modern distributed systems.